Customized cybersecurity training programs
Staying ahead of cybercriminals is tough. Jericho Security’s AI-powered platform offers customized cybersecurity training courses for your employees. Facing new threats or need a topic beyond our library? We deliver custom video content within 72 hours. Keep your employees prepared and your business safe.
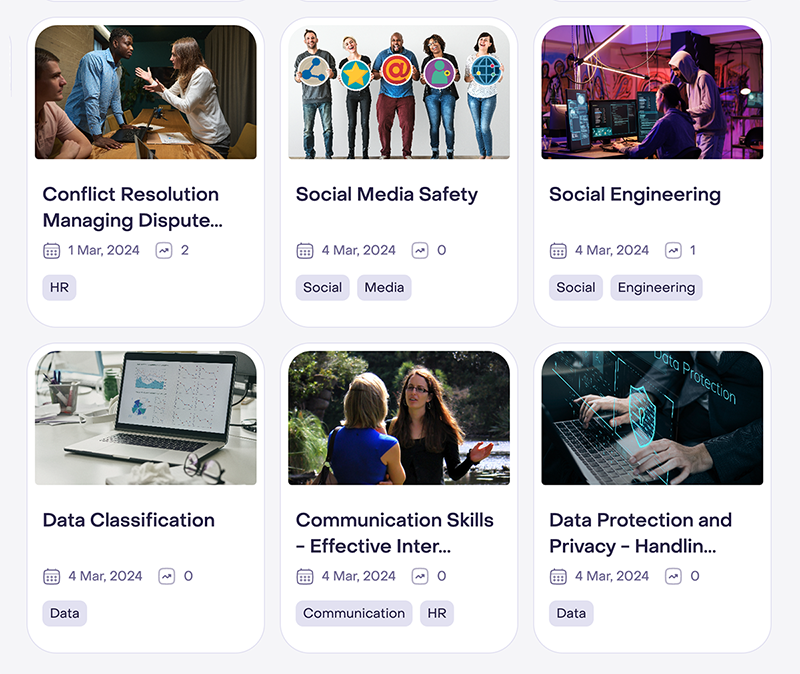
Cybersecurity training courses for employees
Manage your organization's security from a single dashboard. Create and run phishing simulations, deliver custom training, and monitor employee performance.
Tailored to your organization
You know what your team needs better than anyone. Our customized training content is built to match your specific requirements, helping you address industry-specific challenges or meet particular compliance standards.

Quick response when you need it
Cyber threats can pop up fast, but you won’t be left scrambling. Jericho offers end-user phishing training and other important content within 72 hours, so your team is always ready to tackle new threats.

Targeted training for current threats
Keep your business safe by responding to rising threats as they happen. Jericho’s platform delivers employee cybersecurity training that directly addresses the latest vulnerabilities in your industry, helping you stay prepared.

How do Jericho’s cybersecurity training courses for employees work?

Customized training programs
Facing new cyber threats or need more topics? We offer tailored video content just for you.
Pinpoint your employee cybersecurity training needs
Identify the areas where your team could use extra help. Whether it’s strengthening your defenses against phishing or preparing for new threats, Jericho's platform makes it easy to request the training you need.
Submit your security training request
Once you’ve identified what you need, simply submit a request through our platform. Whether you’re dealing with new cyber risks or specialized organizational needs, we’ll respond quickly.
Receive your customized cybersecurity training content
In just 72 hours, you’ll get customized information security training for your employees created to match your request. These video-based modules are designed to engage your employees and help them build the skills they need.
Deploy the information security training for your employees
Easily share the new training with your team. Our platform allows them to access the modules on demand, so they can complete the training when it works best for them.
Get to know the platform
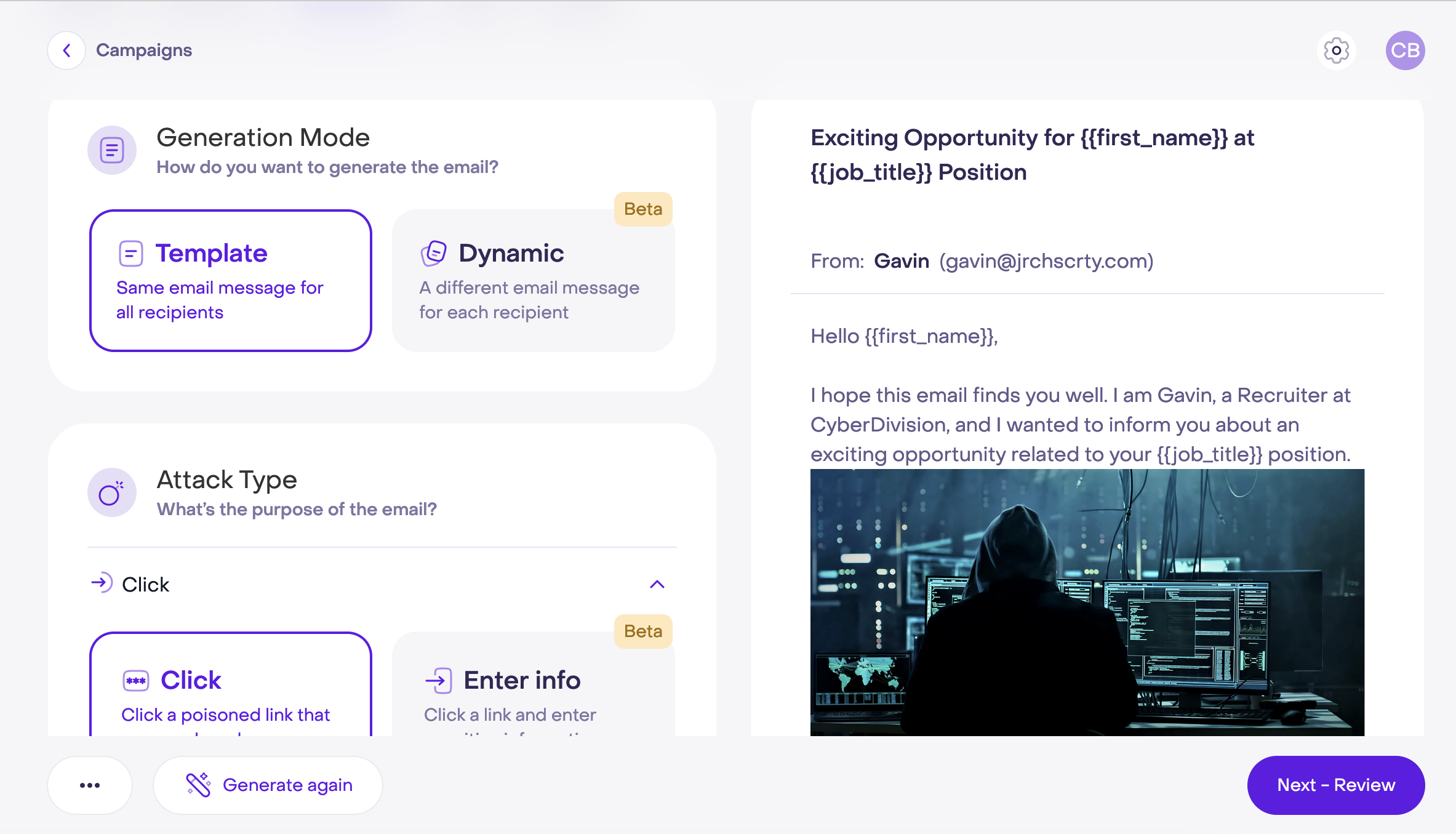
Our AI-driven platform builds training content that’s tailored to your team and industry, helping you address current cyber threats and stay prepared for the future.
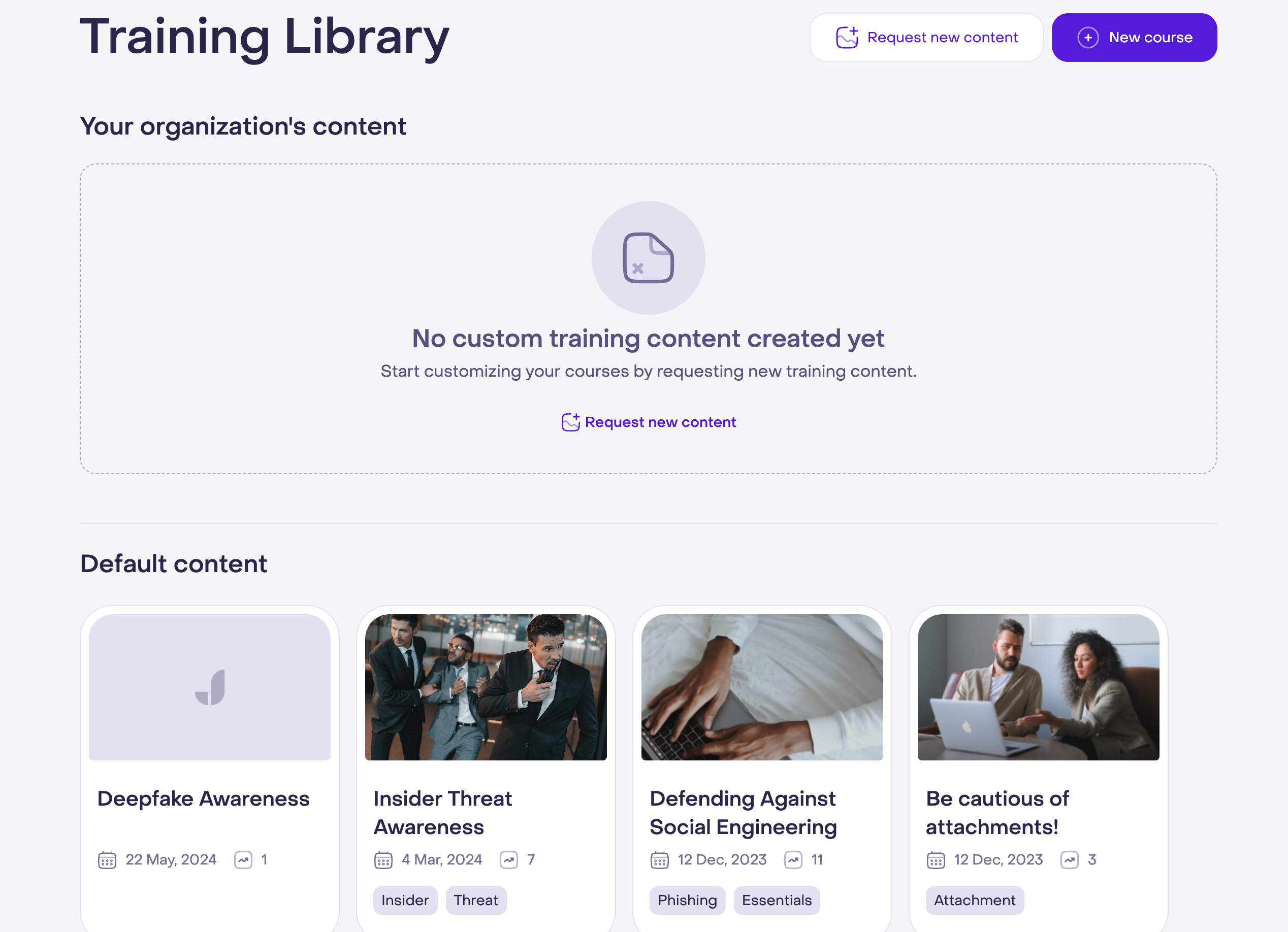
Jericho’s platform is simple to use, so you can request, receive, and deliver customized training content quickly without any hassle.
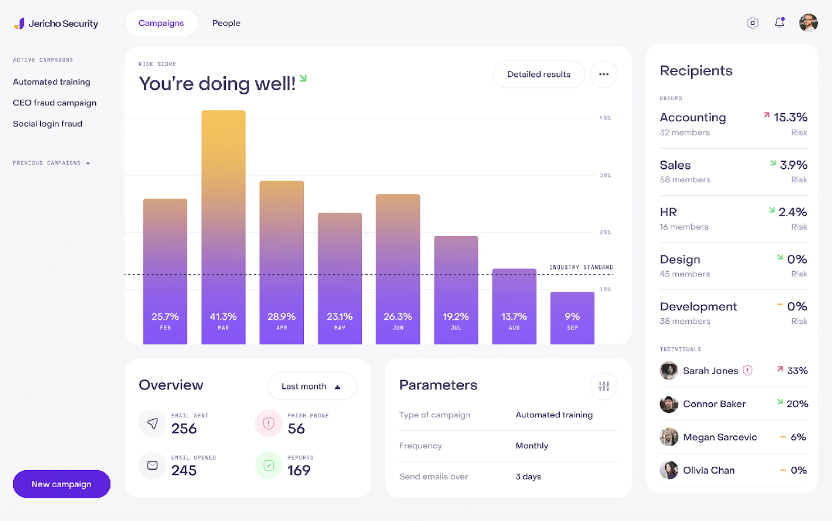
You can track your team’s progress with detailed analytics that show who’s completed the customized training programs, their results, and the effectiveness of the content.
Experience our customized cybersecurity employee training programfor yourself
Customized cybersecurity training courses for employees
Why customize our organization’s IT security training for employees?
Your business has its own set of challenges. With customized training content, you can give your employees the training they need to handle specific risks and industry requirements.
What types of cyber threats can custom training help with?
Jericho’s custom training covers a wide range of threats, including phishing, malware, social engineering, and ransomware. It’s built to tackle the threats that target your organization.
Does personalized training drive behavioral change?
Yes. End user phishing training and other tailored content engage employees in a way that’s easy to understand, helping them build better habits that reduce your risk of a successful cyberattack.
What types of phishing attacks can it simulate?
Jericho Security’s platform allows you to simulate various phishing attack types, including urgent payment requests, personal information updates, and other common themes. You can customize each simulation to reflect the threats your organization is most likely to encounter, making the training more relevant.
Ready to get started?
Don’t wait until it’s too late. Keep your team prepared and your business secure with Jericho’s customized training content. Whether you’re facing new cyber threats or need tailored training for your organization, we’ve got you covered. Contact us today and see how Jericho can help you stay one step ahead with your cybersecurity.
See what else Jericho has to offer
Phishing Simulator
Create customized phishing simulations at the click of a button.
Cybersecurity Dashboard
Manage all your cybersecurity needs in one powerful, easy-to-use platform.
Performance Analytics
Track employee performance in simulations and training.
Our industry training and solutions
At Jericho Security, we specialize in delivering innovative cybersecurity training tailored for a diverse range of industries. Our expertise extends across:
Retail
Protect customers' personal and payment information from data breaches and cyber-attacks.
Learn MoreProtect customers' personal and payment information from data breaches and cyber-attacks.
Learn MoreManufacturing
Keep your production lines and intellectual property secure with cybersecurity solutions.
Learn MoreKeep your production lines and intellectual property secure with cybersecurity solutions.
Learn MoreE-Commerce
Protect your online business from cyber threats while delivering a safer shopping experience.
Learn MoreProtect your online business from cyber threats while delivering a safer shopping experience.
Learn MoreEnergy
Safeguard critical infrastructure with targeted cybersecurity measures.
Learn MoreSafeguard critical infrastructure with targeted cybersecurity measures.
Learn MoreTechnology
Anticipate, identify, and mitigate the latest threats in the fast-paced tech industry.
Learn MoreAnticipate, identify, and mitigate the latest threats in the fast-paced tech industry.
Learn MoreFederal Government
Protect sensitive information with tools designed for the public sector.
Learn MoreProtect sensitive information with tools designed for the public sector.
Learn MoreFinancial Services
Secure your financial operations with solutions tailored to financial services.
Learn MoreSecure your financial operations with solutions tailored to financial services.
Learn MoreState & Local Government
Address the specific cybersecurity needs of state and local governments.
Learn MoreAddress the specific cybersecurity needs of state and local governments.
Learn MoreHealthcare
Keep patient data confidential and secure with compliant security solutions.
Learn MoreKeep patient data confidential and secure with compliant security solutions.
Learn MoreHigher Education
Protect the personal and academic information of your students and staff.
Learn MoreProtect the personal and academic information of your students and staff.
Learn More