Jericho Security’s phishing simulator
Identify vulnerabilities and provide your employees with comprehensive phishing simulation training to teach them how to recognize phishing attacks. Easily launch no-code ultra-personalized phishing simulations in minutes and put your employees’ know-how to the test.
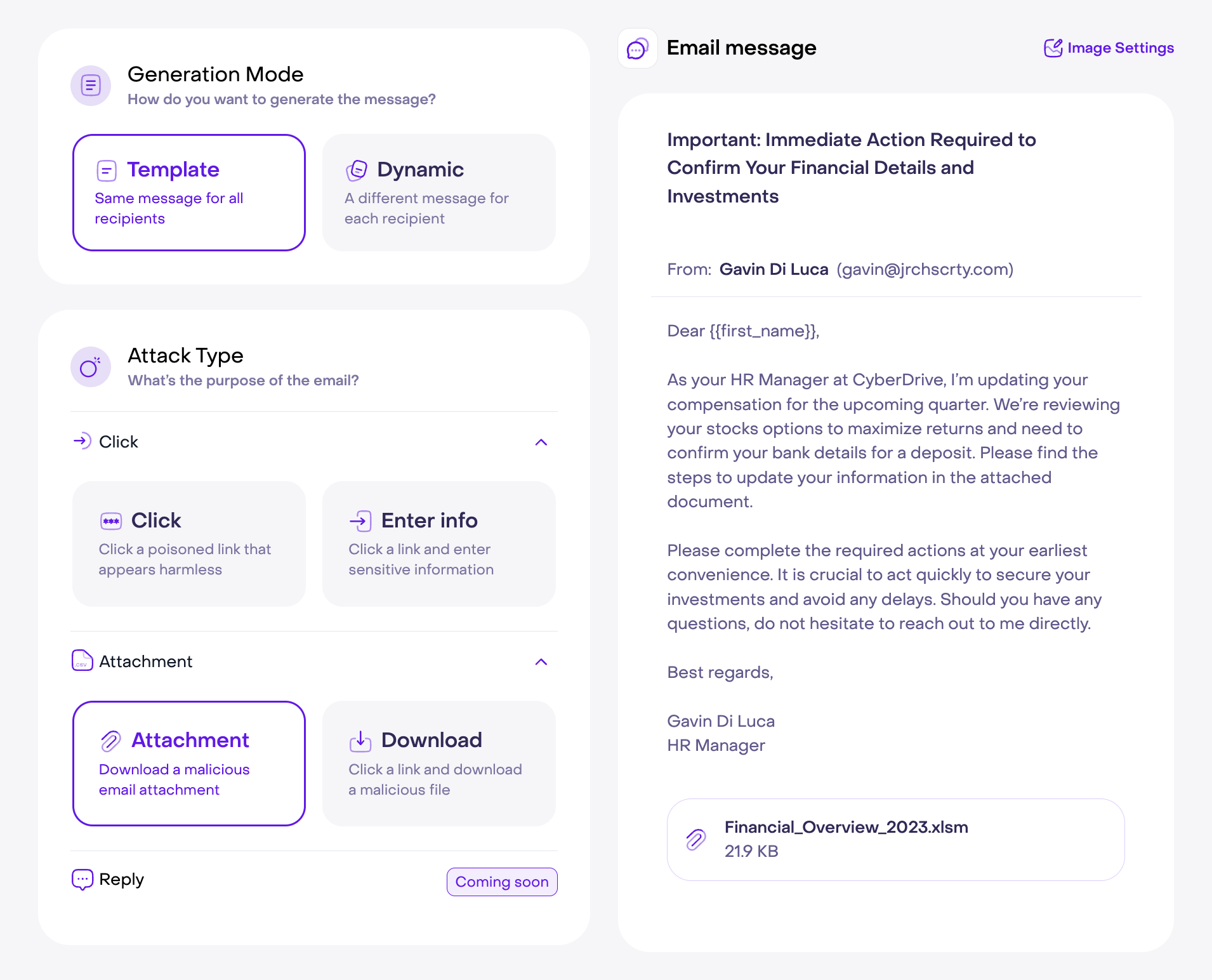
Empower employees to identify phishing emails with AI cybersecurity training
Our AI-driven phishing simulator simplifies cybersecurity training. Build and launch custom simulated phishing emails in minutes through simple multiple-choice selections. There’s no need for coding or complex integrations – just a few clicks, and you’re ready to send your campaign.
AI-generated phishing simulations
Let our AI phishing simulator take on the hard work, crafting realistic phishing simulations that mirror the most current threats, including conversational phishing and deepfake phishing simulation scenarios. Easily challenge employees with complex campaigns, all without the hassle of building them from scratch.

Ultra-personalized campaigns
Tailor each phishing simulation to fit your organization by customizing the email subject, requested information, and more. Add names, company, and department to boost realism and effectively test your employees' awareness.

Create and schedule in minutes
Set up and schedule phishing simulations in just a few clicks. Whether launching a campaign now or planning for later, the process is streamlined, user-friendly, and allows for easy tracking to improve future training.

How does Jericho's phishing simulator dashboard work?
1. Add recipients to the phishing email simulator
Start by selecting who will receive the simulated phishing emails. You can choose to add individuals, groups, or whole contact lists to the phishing email simulator – whatever works best for your phishing simulation campaign.
2. Choose attack type
Select whether you want recipients to click on a link, open an attachment, or enter their personal information. These common phishing tactics help your employees recognize real threats.
3. Customize your email campaign
Personalize the campaign to make it convincing. Choose pretexts like LinkedIn requests, urgent proposals, or gift card offers. Use trends or let our AI suggest the best approach.
4. Choose your sender
Customize further by selecting target information, such as names, departments, or job titles, and defining the sender's details to create a more realistic and convincing simulation.
5. Generate and schedule your campaign
Review your phishing simulator campaign details and then choose whether to launch it immediately or schedule it for later. You have full control over when and how the simulation is delivered.
6. Analyze your results
After the campaign, view detailed analytics on employee responses. Check metrics like email opens, clicks, and form submissions to pinpoint areas needing further training.
See the phishing simulator in action
FAQs on Phishing Simulators
What is a phishing simulator?
A phishing simulator is a tool that lets you create realistic, fake phishing emails to test and train your employees. Reviewing your team’s performance offers insights into your organization’s resilience to phishing attacks and helps identify areas where your team might benefit from additional cybersecurity training. Phishing simulations provide a safe learning environment, allowing employees to practice identifying phishing emails before they encounter the real thing.
Are phishing simulations effective?
Yes, phishing simulations are very effective in raising awareness and helping your employees avoid falling for real phishing attacks. When you use these phishing simulations, you're giving your team hands-on practice in a safe environment. Over time, regular phishing simulations can significantly lower the chances of your employees getting tricked by a real attack, making your organization safer and more secure.
What is the fail rate for phishing simulations?
The failure rate varies depending on the organization's current level of awareness. However, regular simulations tend to lower the fail rate over time as employees become more familiar with phishing tactics.
What are the benefits of phishing simulations?
Phishing simulations are a powerful way to boost cybersecurity awareness in your organization. Regularly running simulations helps your employees recognize potential threats before they cause harm. They also empower your organization to address new threats as they arise, keeping your team up-to-date on the latest tactics used by cybercriminals.
Can phishing simulations include targeted spear-phishing scenarios?
Yes. Phishing simulation tools can replicate targeted spear-phishing campaigns by using personalized details such as names, departments, or job roles. This helps train employees to recognize even the most convincing threats.
How often should we run phishing simulation training?
Running phishing simulations quarterly is a good baseline, but many organizations see better results with monthly or bi-monthly tests. Frequent exposure reinforces awareness and reduces your phishing simulation fail rate over time.
Can we simulate conversational phishing attacks?
Absolutely. Conversational phishing involves ongoing back-and-forth emails to build trust before a malicious request is made. Including these in your AI-driven phishing simulations helps employees spot threats that unfold over multiple messages.
What is a deepfake phishing simulation?
A deepfake phishing simulation uses AI-generated audio or video to impersonate a trusted person, such as a CEO or manager, as part of a phishing attack. Training against this type of threat prepares your team for emerging, sophisticated cyber risks.
What happens if an employee fails a phishing simulation?
When an employee clicks a link or submits information in a simulated phishing email, they can be redirected to instant, targeted training content. This reinforces the lesson right away, making it more memorable and effective.
Ready to try Jericho's phishing simulator?
Jericho Security’s phishing simulator is a fast, easy way to strengthen your organization’s defenses against phishing attacks. Get started today and see how simple it is to protect your business.
See what else Jericho has to offer
Cybersecurity Dashboard
Manage all your cybersecurity needs in one powerful, easy-to-use platform.
Customized Training Content
Tailored training videos available on demand for more impactful results.
Performance Analytics
Track and analyze employee performance in simulations and training.
Our industry training and solutions
At Jericho Security, we specialize in delivering innovative cybersecurity training tailored for a diverse range of industries. Our expertise extends across:
Retail
Protect customers' personal and payment information from data breaches and cyber-attacks.
Learn MoreProtect customers' personal and payment information from data breaches and cyber-attacks.
Learn MoreManufacturing
Keep your production lines and intellectual property secure with cybersecurity solutions.
Learn MoreKeep your production lines and intellectual property secure with cybersecurity solutions.
Learn MoreE-Commerce
Protect your online business from cyber threats while delivering a safer shopping experience.
Learn MoreProtect your online business from cyber threats while delivering a safer shopping experience.
Learn MoreEnergy
Safeguard critical infrastructure with targeted cybersecurity measures.
Learn MoreSafeguard critical infrastructure with targeted cybersecurity measures.
Learn MoreTechnology
Anticipate, identify, and mitigate the latest threats in the fast-paced tech industry.
Learn MoreAnticipate, identify, and mitigate the latest threats in the fast-paced tech industry.
Learn MoreFederal Government
Protect sensitive information with tools designed for the public sector.
Learn MoreProtect sensitive information with tools designed for the public sector.
Learn MoreFinancial Services
Secure your financial operations with solutions tailored to financial services.
Learn MoreSecure your financial operations with solutions tailored to financial services.
Learn MoreState & Local Government
Address the specific cybersecurity needs of state and local governments.
Learn MoreAddress the specific cybersecurity needs of state and local governments.
Learn MoreHealthcare
Keep patient data confidential and secure with compliant security solutions.
Learn MoreKeep patient data confidential and secure with compliant security solutions.
Learn MoreHigher Education
Protect the personal and academic information of your students and staff.
Learn MoreProtect the personal and academic information of your students and staff.
Learn More