Measure employee performance analytics
You track KPIs for sales, productivity, and customer satisfaction. Why not for cybersecurity? With Jericho's employee performance analytics, measure how well your team defends against threats like phishing. By monitoring key behaviors, you'll gain insights to strengthen your strategy and help your team improve where it matters most.
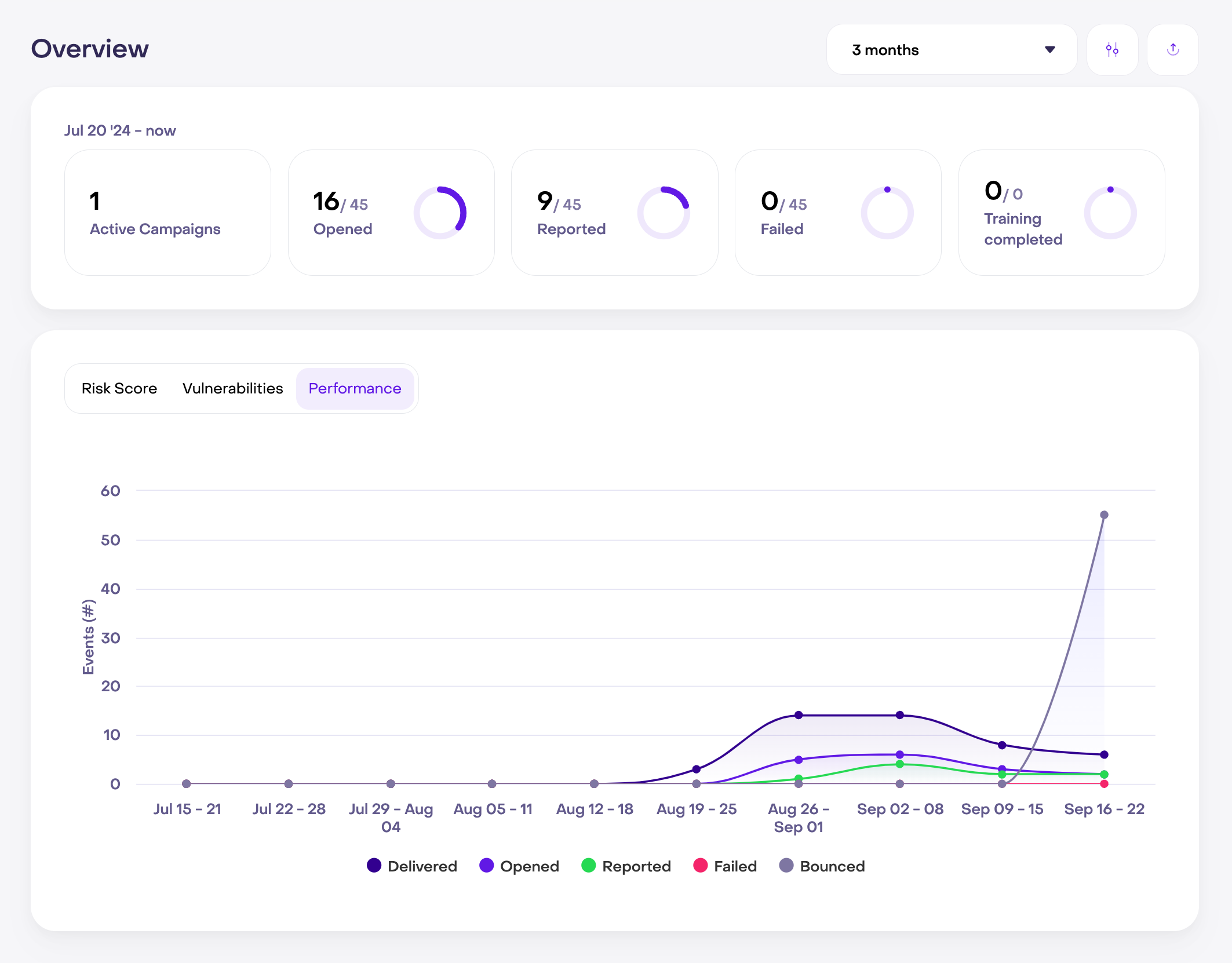
Employee performance metrics unpacked
Our AI-driven phishing simulator simplifies cybersecurity training. Build and launch custom phishing simulations in minutes through simple multiple-choice selections. There’s no need for coding or complex integrations – just a few clicks, and you’re ready to send your campaign.
Create phishing campaigns
You can set up phishing simulations tailored to your specific needs. Jericho’s platform makes it easy to create detailed campaigns that effectively test your team’s ability to recognize and respond to phishing emails.

Track employee performance
Get real-time insights into how your team responds to phishing tests. You can track open rates, click rates, fail rates, and report rates, so you can see exactly where you need to focus your training efforts.

Run custom training based on results
After reviewing the data, you can assign custom cybersecurity training to employees who need extra help. This targeted approach ensures that everyone improves their cybersecurity skills, making your organization safer overall.

How does Jericho’s employee performance analytics platform work?
Create phishing simulations
Start by creating phishing simulations tailored to your industry and the specific risks your employees face. Jericho’s easy-to-use platform allows you to customize these tests with just a few clicks.
Schedule and run
Deploy the phishing tests across your organization. Track how employees respond, from who opens the email to who clicks on a malicious link or reports it to your IT team.
Analyze team results
Jericho provides detailed analytics on employee performance metrics like open rates, click rates, fail rates, and report rates to see how each employee or department is handling phishing threats.
Implement custom training based on
employee performance metrics
Based on the results, you can assign targeted training to employees who need it most. This ensures that everyone is improving their skills where it’s needed.
Your organization's dashboard is packed with customizable security features designed to meet your needs.
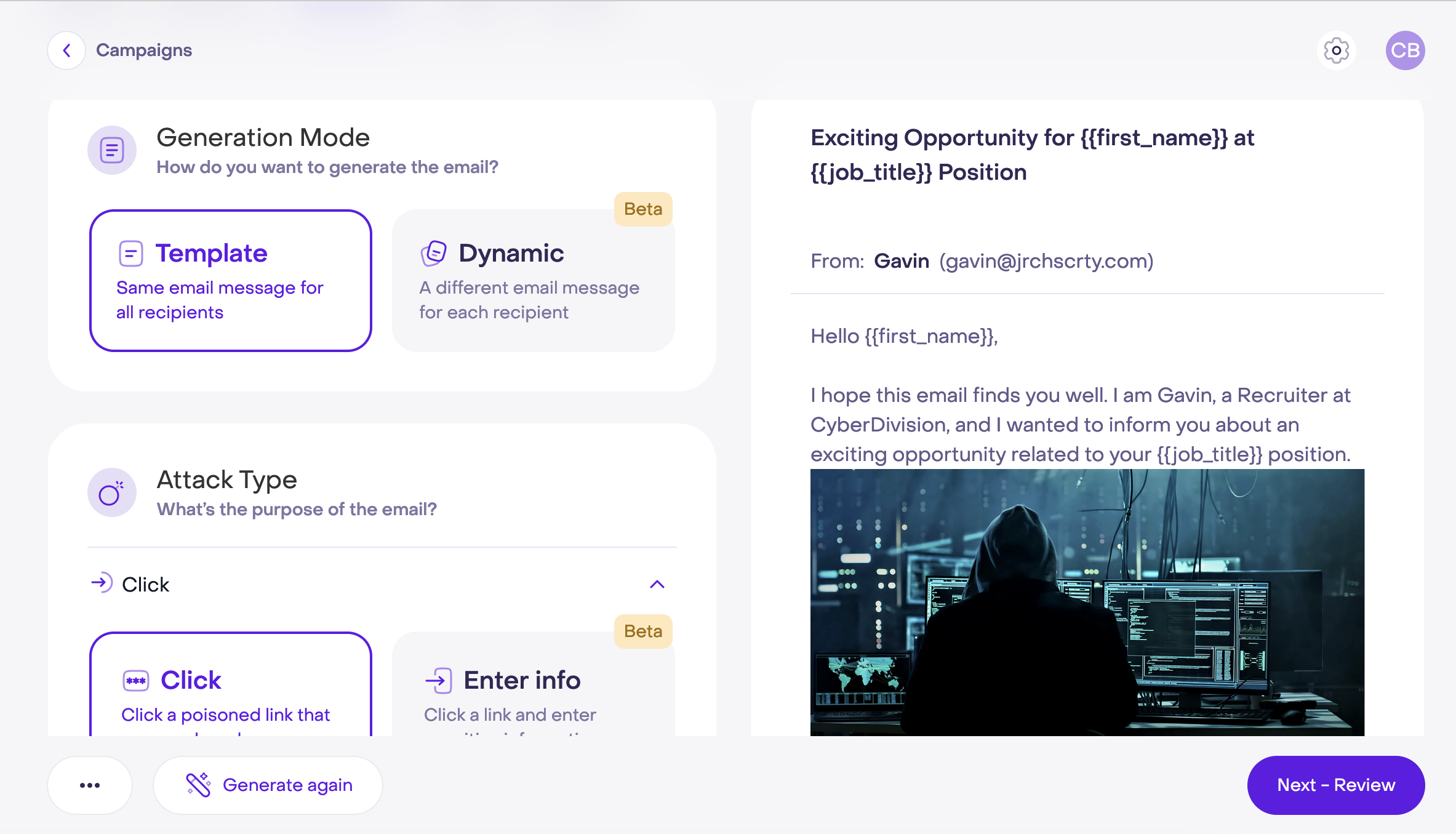
Jericho’s platform lets you create phishing simulations quickly and easily. Customize your campaigns to reflect the real-world threats your team is likely to face.
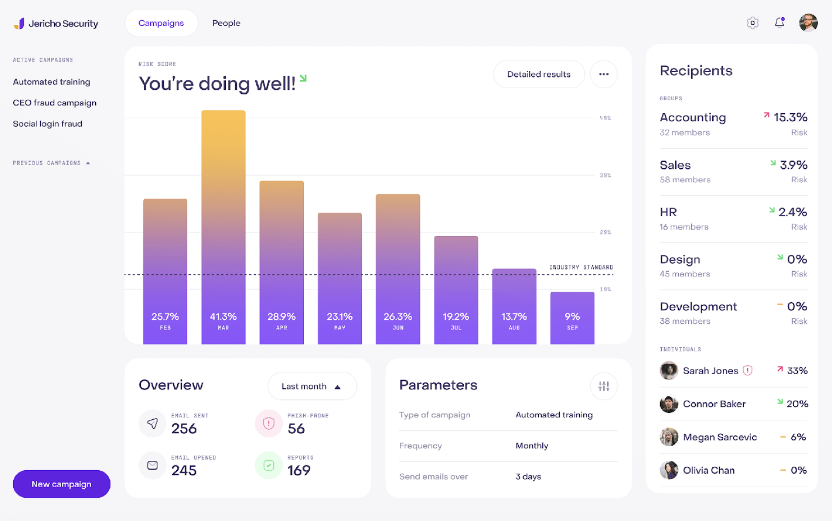
Track and measure employee behavior with in-depth analytics that show how well they handle phishing tests, including metrics like open rates and report rates.
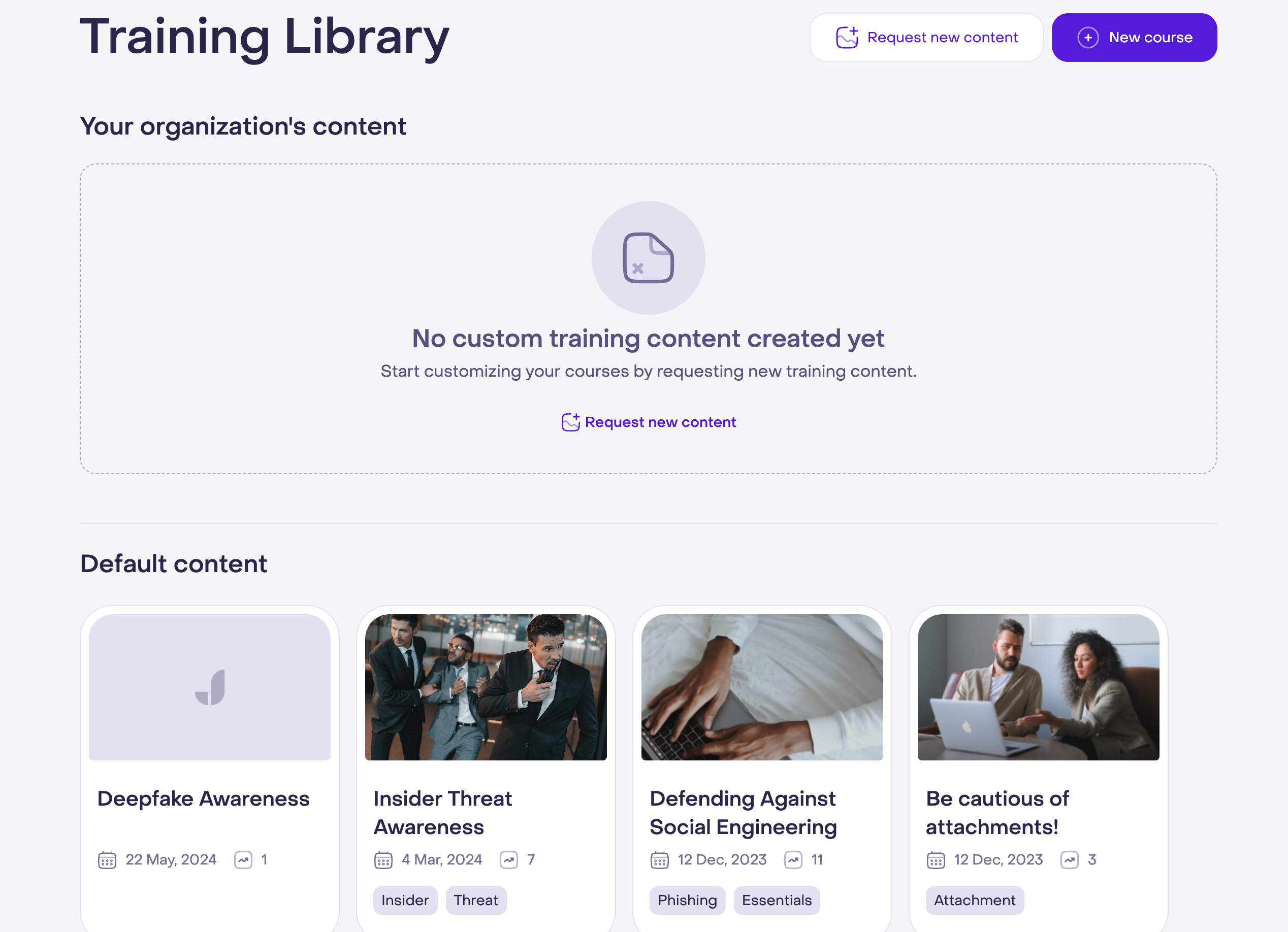
Assign training modules based on employee key performance indicators. This ensures that each team member receives the training they need to improve, making your security strategy more effective.
Would Your Employees Pass
a Phishing Test?
Phishing attacks can happen at any time. Are your employees ready? Assess your team’s cybersecurity know-how by running a custom phishing simulation.
Keep on top of employee performance in cybersecurity
What is employee performance analytics in cybersecurity?
Employee cybersecurity performance measures how well your employees respond to potential cyber threats, such as phishing emails. It tracks key metrics like open rates, click rates, and report rates to give you a clear picture of how your team is performing.
How are employee performance analytics and training in cybersecurity connected?
Monitoring employee performance helps you identify areas where your team may be vulnerable to phishing attacks or other cyber threats. This allows you to provide targeted training to improve their skills and protect your business.
How do Jericho’s employee performance analytics help improve company security?
Jericho’s platform gives you real-time data on how employees handle phishing simulations. This data helps you identify weak points and provide the right training to reduce your organization’s risk.
How should I use employee performance metrics?
You can use this data to identify which employees or departments need more training, track progress over time, and measure the effectiveness of your cybersecurity training programs.
See how Jericho's employee performance analytics work
Don’t leave your security to chance. Use Jericho’s employee performance analytics to measure how well your team is prepared for phishing attacks and provide them with the training they need to improve.
See what else Jericho has to offer
Cybersecurity Dashboard
Manage all your cybersecurity needs in one powerful, easy-to-use platform.
Customized Training Content
Tailored training videos available on demand for more impactful results.
Our industry training and solutions
At Jericho Security, we specialize in delivering innovative cybersecurity training tailored for a diverse range of industries. Our expertise extends across:
Retail
Protect customers' personal and payment information from data breaches and cyber-attacks.
Learn MoreProtect customers' personal and payment information from data breaches and cyber-attacks.
Learn MoreManufacturing
Keep your production lines and intellectual property secure with cybersecurity solutions.
Learn MoreKeep your production lines and intellectual property secure with cybersecurity solutions.
Learn MoreE-Commerce
Protect your online business from cyber threats while delivering a safer shopping experience.
Learn MoreProtect your online business from cyber threats while delivering a safer shopping experience.
Learn MoreEnergy
Safeguard critical infrastructure with targeted cybersecurity measures.
Learn MoreSafeguard critical infrastructure with targeted cybersecurity measures.
Learn MoreTechnology
Anticipate, identify, and mitigate the latest threats in the fast-paced tech industry.
Learn MoreAnticipate, identify, and mitigate the latest threats in the fast-paced tech industry.
Learn MoreFederal Government
Protect sensitive information with tools designed for the public sector.
Learn MoreProtect sensitive information with tools designed for the public sector.
Learn MoreFinancial Services
Secure your financial operations with solutions tailored to financial services.
Learn MoreSecure your financial operations with solutions tailored to financial services.
Learn MoreState & Local Government
Address the specific cybersecurity needs of state and local governments.
Learn MoreAddress the specific cybersecurity needs of state and local governments.
Learn MoreHealthcare
Keep patient data confidential and secure with compliant security solutions.
Learn MoreKeep patient data confidential and secure with compliant security solutions.
Learn MoreHigher Education
Protect the personal and academic information of your students and staff.
Learn MoreProtect the personal and academic information of your students and staff.
Learn More