Jericho Security's cybersecurity dashboard
Protect your organization against evolving threats with Jericho Security's all-in-one cybersecurity executive dashboard and security analytics platform.
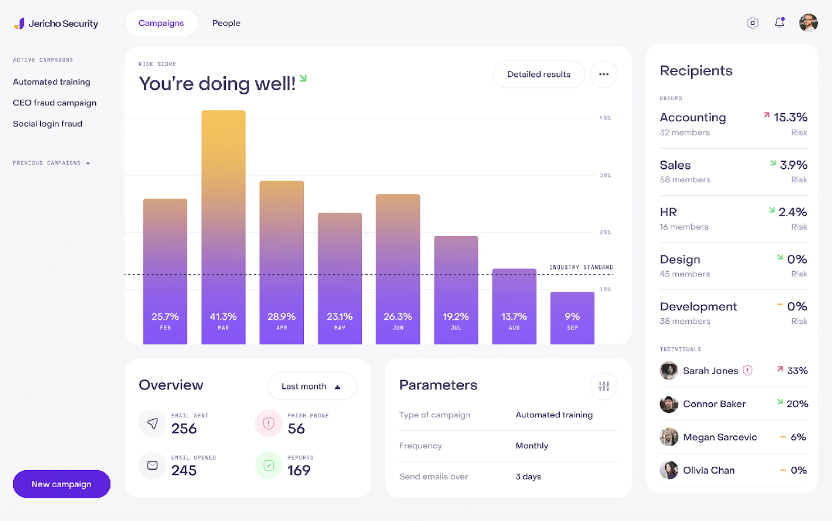
Centralized employee digital security management dashboard
Manage your organization's security from a single intuitive interface. Create and run phishing simulations, deliver custom training, and monitor employee performance. All from one powerful CISO dashboard.
Create email campaigns
Create campaigns from templates or build dynamic emails from scratch. Select the phishing attack type, and customize every detail – from the language and style to the inclusion of images and logos.

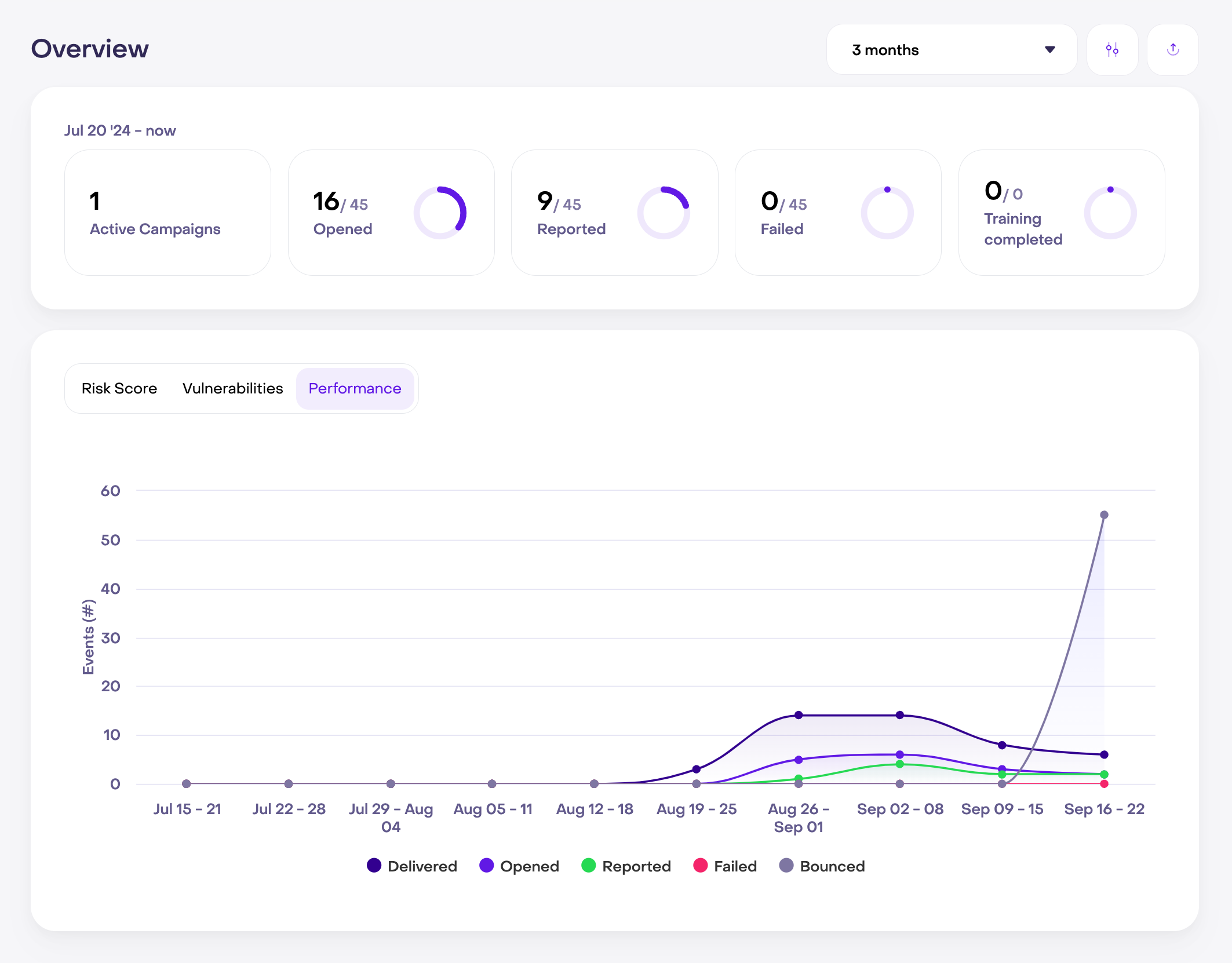
Track employee performance
The cybersecurity metrics dashboard offers detailed analytics on employee performance in phishing simulations. Monitor individual and group results, spot vulnerabilities, and assign targeted training to address weaknesses.

Seamless integration and scalability
Jericho Security’s platform integrates seamlessly with your systems, making it easy to incorporate. As your organization grows, the information security dashboard scales to manage more users and expand security without disruption.

How does Jericho's CISO dashboard work?

Cybersecurity Dashboard Overview
With Jericho Security's dashboard, you can manage your organization's cybersecurity training with ease. The platform also supports the generation of cybersecurity risk assessment reports, helping you evaluate and communicate your organization’s security posture effectively.
IT security dashboard for creating anti-phishing campaigns
Set up phishing simulations tailored to the specific needs of your organization. You can select the type of phishing attack, customize the email content in detail, and target individuals or groups based on department, role, or other relevant factors.
Manage users
The "People + Groups" section of the dashboard allows you to train your workforce more effectively. You can add employees, group them by categories, and assign targeted training based on their roles or previous performance in security assessments.
Access and assign training content
The training library features a wide range of cybersecurity topics, including deepfakes, social engineering, and mobile security. You can easily assign training to individuals or groups, ensuring that your entire organization is always well-prepared.
Request custom training content
If you need training on a topic not covered in the existing library, request custom content and we’ll deliver in under 24 hours. Quickly implement new training to address emerging threats or specific organizational needs.
Your organization's digital security dashboard is packed with customizable features designed to meet your needs.
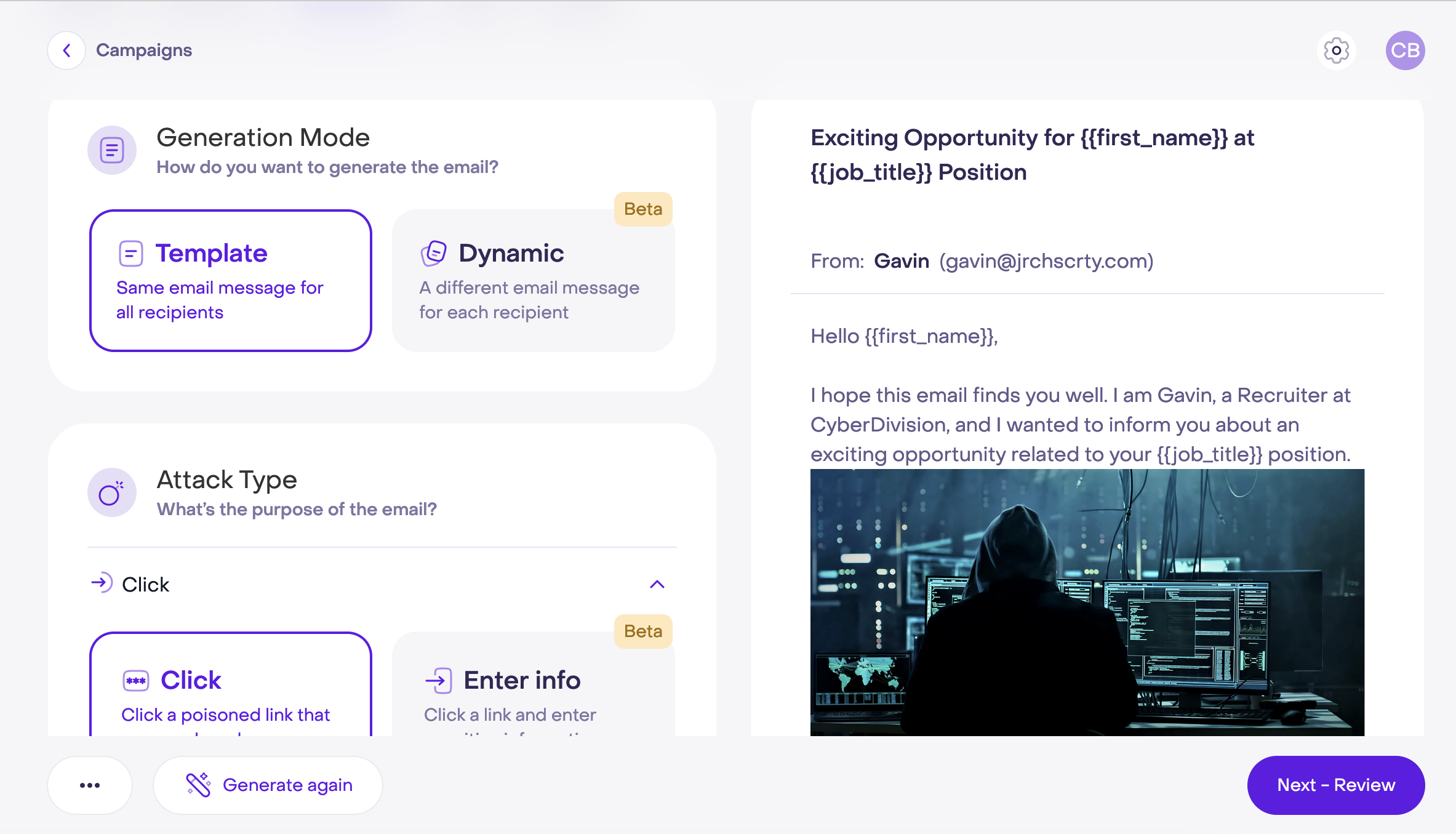
Phishing Simulation Tools
Create realistic phishing campaigns that test your employees' ability to identify and respond to threats. With its personalization options and variety of attack types, the platform makes cybersecurity training a breeze.
Get a Demo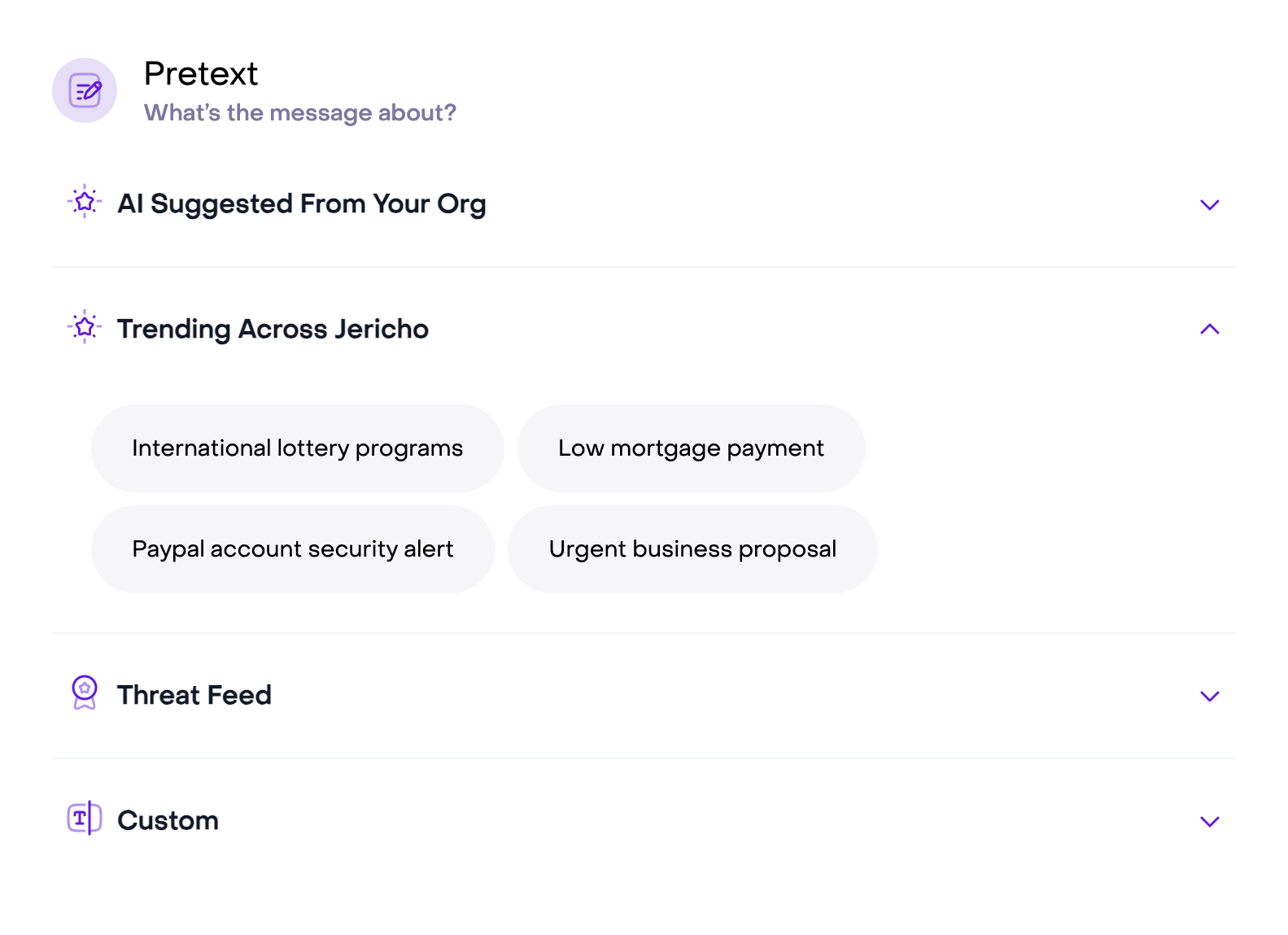
Topic Selection for Phishing Simulations
Tailor your phishing simulations by choosing from a range of relevant topics such as urgent payment requests, personal information updates, and other popular themes. You can craft scenarios that closely mirror the types of phishing attacks your organization might encounter, making the training more effective and realistic.
Advanced Analytics and Reporting
Using the dashboard, you can track the effectiveness of phishing simulations, monitor training progress, and identify concerning trends. These detailed cybersecurity KPI dashboard reports empower you to make data-driven decisions that improve your overall cybersecurity strategy.
Understanding the cybersecurity executive dashboard
What is a cybersecurity dashboard?
A cybersecurity dashboard is a centralized tool that helps you manage your organization's security operations. The digital security dashboard includes phishing simulations, training, and user performance. It provides a single interface where you can monitor, assess, and improve your cybersecurity practices, making it easier to protect your business from threats.
How can a cybersecurity platform improve security?
A cybersecurity platform allows you to quickly identify vulnerabilities, assign targeted training, and monitor employee performance – all in one place. By providing real-time data and insights, a cybersecurity metrics dashboard can help you make informed decisions that improve your organization's security and reduce the risk of cyber attacks.
What types of training content are available?
Jericho Security's training library covers a wide range of cybersecurity topics, from basic awareness to advanced threat detection. Topics include social engineering, malware, mobile security, and more. If you need training on a specific topic not covered in the library, you can request custom content tailored to your organization's needs.
What types of phishing attacks can it simulate?
Jericho Security’s platform allows you to simulate various phishing attack types, including urgent payment requests, personal information updates, and other common themes. You can customize each simulation to reflect the threats your organization is most likely to encounter, making the training more relevant.
What is the purpose of a cybersecurity KPI dashboard?
It helps CISOs and security leaders measure the effectiveness of security programs through key performance indicators like phishing simulation success rates and training completion.
How does a security analytics platform improve organizational resilience?
By offering real-time insights, predictive analytics, and customizable dashboards, Jericho’s platform helps organizations proactively manage cybersecurity threats.
What makes Jericho’s information security dashboard different?
Our dashboard combines real-time analytics, AI-driven training, and full-spectrum threat simulation to provide an integrated and responsive cybersecurity solution.
Ready to Get Started?
See what else Jericho has to offer
Customized Training Content
Tailored training videos available on demand for more impactful results.
Performance Analytics
Track and analyze employee performance in simulations and training.
Our industry training and solutions
At Jericho Security, we specialize in delivering innovative cybersecurity training tailored for a diverse range of industries. Our expertise extends across:
Retail
Protect customers' personal and payment information from data breaches and cyber-attacks.
Learn MoreProtect customers' personal and payment information from data breaches and cyber-attacks.
Learn MoreManufacturing
Keep your production lines and intellectual property secure with cybersecurity solutions.
Learn MoreKeep your production lines and intellectual property secure with cybersecurity solutions.
Learn MoreE-Commerce
Protect your online business from cyber threats while delivering a safer shopping experience.
Learn MoreProtect your online business from cyber threats while delivering a safer shopping experience.
Learn MoreEnergy
Safeguard critical infrastructure with targeted cybersecurity measures.
Learn MoreSafeguard critical infrastructure with targeted cybersecurity measures.
Learn MoreTechnology
Anticipate, identify, and mitigate the latest threats in the fast-paced tech industry.
Learn MoreAnticipate, identify, and mitigate the latest threats in the fast-paced tech industry.
Learn MoreFederal Government
Protect sensitive information with tools designed for the public sector.
Learn MoreProtect sensitive information with tools designed for the public sector.
Learn MoreFinancial Services
Secure your financial operations with solutions tailored to financial services.
Learn MoreSecure your financial operations with solutions tailored to financial services.
Learn MoreState & Local Government
Address the specific cybersecurity needs of state and local governments.
Learn MoreAddress the specific cybersecurity needs of state and local governments.
Learn MoreHealthcare
Keep patient data confidential and secure with compliant security solutions.
Learn MoreKeep patient data confidential and secure with compliant security solutions.
Learn MoreHigher Education
Protect the personal and academic information of your students and staff.
Learn MoreProtect the personal and academic information of your students and staff.
Learn More